Current Projects
Fine-grained Internet Path Control and DDoS Defense

Enhanced Security and Efficiency in Sorting Centers through Computational Robotics
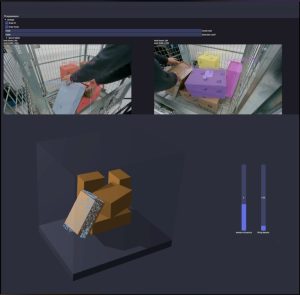
The Computational Robotics Lab (CRL) and Swiss Post are collaborating to enhance security and efficiency in their sorting centers. This project enables pose estimation, reconstruction and segmentation of parcels in cluttered environments, as well as tracking of the parcels through their lifecycle at a center from different camera streams.
 In today’s digital era, cybersecurity knowledge is crucial, but existing platforms often cater to professionals or impose entry barriers for younger learners. This project seeks to address this gap by creating a browser-based learning platform for high-school students. Featuring a lesson center and a small mock-up social media website, the platform provides accessible cybersecurity education. The social media platform contains intentional vulnerabilities which allow students to explore security-related topics in a hands-on manner. This approach aims at bridging the accessibility gap in cybersecurity education.
In today’s digital era, cybersecurity knowledge is crucial, but existing platforms often cater to professionals or impose entry barriers for younger learners. This project seeks to address this gap by creating a browser-based learning platform for high-school students. Featuring a lesson center and a small mock-up social media website, the platform provides accessible cybersecurity education. The social media platform contains intentional vulnerabilities which allow students to explore security-related topics in a hands-on manner. This approach aims at bridging the accessibility gap in cybersecurity education.
Enhancing Art Engagement with Character-Driven Augmented Reality
Industry partner: Swiss Post
The Game Technology Center (GTC) and the Swiss Post collaborate to enhance accessibility and engagement with the Swiss Post’s art collection. Through the development of an AR mobile app, users will explore virtual artworks, guided by a virtual character.
Prioritizing Cybersecurity Controls based on Coverage of Attack Techniques

Industry partner: Zurich Insurance
Organizations face a wealth of possible cybersecurity threats, ranging from purely technological, such as vulnerability exploitation on software running on their systems, to human deception, such as phishing. There exist several attempts at describing and categorizing possible attack vectors at various levels of abstraction. For example, the MITRE ATT&CK knowledge base of adversary tactics and techniques is a comprehensive list of detailed attack techniques that have been observed in practice. There have been attempts to describe and categorize implementable controls or mitigations to prevent or mitigate such attacks, notably, the NIST Special Publication 800-53. The number of possible controls is usually big and organizations commonly have limited budgets to implement them. Interestingly, it has been observed that there is fat-tailed distribution in the number of attacks that are mitigated by the NIST 800-53 controls. A natural question is thus, out of the possible attack vectors observed in practice, which are the more likely to happen? Is it possible, given a mapping from controls to attacks, and a notion attack probability and/or severity to come up with a priority ordering on the controls to implement?
 Industry partner: Swiss Post
Industry partner: Swiss Post
Softwares often have security vulnerabilities and can be attacked by adversaries, with potentially significant negative social or economic consequences. To protect themselves, organizations have increasingly relied on bug bounty programs, where external individuals probe the system and report any vulnerabilities (bug) in exchange for monetary rewards (bounty). Our project aims to offer insights into how to design such bug bounty schemes with tools from game theory and mechanism design.
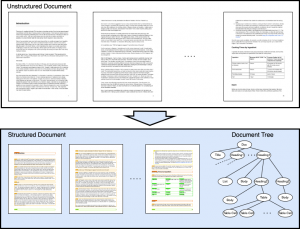
Enhancing Document Processing with Hierarchical Structure
 Today, the SCION Internet architecture is serving a variety of real-world use cases. However, without SBAS, it is not possible to carry the benefits of SCION out into the wider Internet. This system creates a seamless bridge between SCION and the existing Internet to expand the reach of services built on top of modern Internet architectures.
Today, the SCION Internet architecture is serving a variety of real-world use cases. However, without SBAS, it is not possible to carry the benefits of SCION out into the wider Internet. This system creates a seamless bridge between SCION and the existing Internet to expand the reach of services built on top of modern Internet architectures.
Communication, in particular for critical infrastructures, requires a high level of availability that remains available despite earthquakes, power outages, misconfigurations, or network attackers. One example is the financial industry, which has high requirements on availability to ensure that up-to-date trading information is accessible, that financial transactions are executed within short time windows, and that end customers can execute banking applications online.
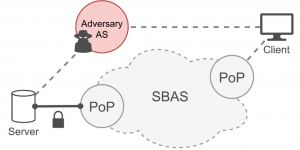 Today, the SCION Internet architecture is serving a variety of real-world use cases. However, without SBAS, it is not possible to carry the benefits of SCION out into the wider Internet. This system creates a seamless bridge between SCION and the existing Internet to expand the reach of services built on top of modern Internet architectures.
Today, the SCION Internet architecture is serving a variety of real-world use cases. However, without SBAS, it is not possible to carry the benefits of SCION out into the wider Internet. This system creates a seamless bridge between SCION and the existing Internet to expand the reach of services built on top of modern Internet architectures.
 Industry partner: NEC
Industry partner: NECIn this project, NEC and ETH are aiming to address various issues in cloud and blockchain security in order to improve the security and scalability of existing storage services. First, in the area of blockchain technology our project focuses on the security and privacy of different blockchain technologies and on the development of new protocols and systems to enhance functionality. Second, in the area of cloud security our projects investigated secure data deduplication that allows storage reduction and makes cloud storage financially attractive to customers, along with novel access control paradigms that allow data sharing according to end users’ needs.
 Industry partner: NEC
Industry partner: NEC
Maintaining security and privacy in 5G is highly challenging because 5G connects every aspect of our online life to the network, providing connectivity for much critical data stored or shared online. In this project, NEC and ETH are aiming to enhance the security of 5G networks by building a new 5G network slicing architecture that enables: i) dynamic network isolation of mobile devices, ii) network slicing over WAN (Wide-Area Network), iii) secure access control, and iv) scalable key establishment and management.
Inter-domain routing is at the heart of the Internet, yet little effort has been spent on building a formally verified secure routing protocol. In this project, we verify the next-generation routing protocol SCION, from high-level properties down to the implementation. We prove the security of the protocol in the symbolic model and extract a specification of the IO-behavior of SCION routers from it using refinement. On the code level this specification is used to prove the correctness of the implementation. We develop a new technique that establishes a provably sound link between protocol and software verification.
 Industry partner: Swiss Post
Industry partner: Swiss PostPhishing emails – deceptive messages that trick users into revealing sensitive data – are still a major problem in corporate settings. In this project, we aim to improve phishing detection and education, by bringing users into the security loop. We aim to understand the most effective ways to train users to recognize such deceptive emails and to increase awareness. Moreover, we plan to analyze whether user reports of phishing emails can help security, by improving the performance of automatic detection systems.
Furthermore, as automatic detection systems still mostly rely on rules created manually by experts, we aim at understanding whether a Machine Learning driven system could generate high-quality rules from such user reports.
 Secure and precise time synchronization is an essential requirement for many applications. Current best practice to achieve large-scale time synchronization relies on hierarchical networks from a set of primary time servers synchronized with global navigation satellite systems (GNSS) to every end host. However, solely relying on GNSS as a global reference clock comes at the risk of single-point-of-failure. In this project, we aim to develop a scalable, Byzantine fault-tolerant clock synchronization system that does not place trust in any single entity and is resilient to a fraction of faulty or malicious entities.
Secure and precise time synchronization is an essential requirement for many applications. Current best practice to achieve large-scale time synchronization relies on hierarchical networks from a set of primary time servers synchronized with global navigation satellite systems (GNSS) to every end host. However, solely relying on GNSS as a global reference clock comes at the risk of single-point-of-failure. In this project, we aim to develop a scalable, Byzantine fault-tolerant clock synchronization system that does not place trust in any single entity and is resilient to a fraction of faulty or malicious entities.
Debuglets: Programmable Network Debugging Infrastructure
![]()
Industry partner: ZKB
On today’s Internet, end-user debugging is largely limited to primitive tools such as ping and traceroute, supplemented by purpose-built services such as bandwidth measurement, website failure detection, and uptime monitors. Unfortunately, these tools do not provide sufficient data to isolate specific network faults, nor do they give the user results that can be validated by external entities. In this project, we build Debuglets, a distributed network debugging infrastructure that enhances end-user debugging, reduces the time to identify network issues, and provides new business models for ASes.
Secure and Sovereign Smartphone Platform
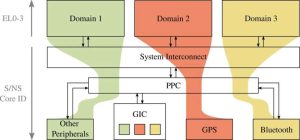 Industry partner: Armasuisse
Industry partner: Armasuisse
The majority of smartphones either run iOS or Android operating systems. This has created two distinct ecosystems largely controlled by Apple and Google. When handling high sensitive information this is far from desirable. Rather, full organizational-level control over all the code (including the OS) that can access sensitive data is needed. In this project, we explore how to give full control to the user while remaining compatible with existing ecosystem — with increased security guarantees.
