Secure and Sovereign Smartphone Platform
Status
This project started in November 2021 and is ongoing.
Researchers
Friederike Groschupp
Mark Kuhne
Dr. Moritz Schneider
Dr. Ivan Puddu
Prof. Shweta Shinde
Prof. Srdjan Capkun
Industry Partner:
Armasuisse
Description
The majority of smartphones either run iOS or Android operating systems. This has created two distinct ecosystems largely controlled by Apple and Google. While they generally provide phones which are rich in functionality, they also constraint what can be done with the devices: the two aforementioned companies dictate which applications can run, how they run, and what kind of phone resources they can access. End-users have no choice but to fully entrust their security and privacy to OS vendors and accept the functionality constraints they impose. When handling high sensitive information, like with our industry partners, this is far from desirable. Rather, organizations need full control over all the code (including the OS) that can access sensitive data (e.g., messaging apps). However, given the wide use of Android and iOS, immediately leaving these ecosystems is not practical, except in niche application areas.
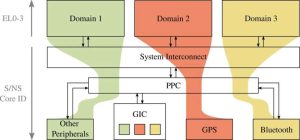
In this project, we explore the development of a new smartphone architecture that securely transfers the control back to users, developers, and organizations while maintaining compatibility with the rich existing smartphone ecosystems (to maintain a high user experience). Specifically, our solution allows mobile users to install and run security-sensitive apps in isolation, thus protecting them from other applications as well as the operating system. The platform will maintain compatibility with legacy operating systems (e.g, Android) and legacy apps (e.g., as provisioned by Android App Store). Thus, the user can run sensitive and non-sensitive applications on the same device.
Our key design choice is to use a hardware-based mechanism called trusted execution environments (TEEs). Using a TEE, we introduce a small security monitor (SM) that executes at the highest privilege on the phone. The SM uses the underlying hardware features to ensure that the security-sensitive applications are isolated from the legacy OS and legacy applications. The SM is not omnipotent in our approach: It can manage apps and the legacy OS, but it cannot inspect their memory or interfere with their execution. We call this the management-without-inspection primitive. Further, the SM ensures that secure apps can access system resources (e.g., Bluetooth) without the legacy OS being able to inspect or interfere.
