Recently, ZISC researchers demonstrated how the new hover (floating touch) technology, available in the latest Android smartphones, can be abused by any application running in background to record all touchscreen input system-wide. By using the newly discovered attack, a malicious application running on the system is able to profile user’s behavior, capture sensitive input such as passwords and PINs as well as record all user’s social interactions. ZISC researchers implemented a system called Hoover, a proof-of-concept malicious application that runs in the system background and records all input to foreground applications.
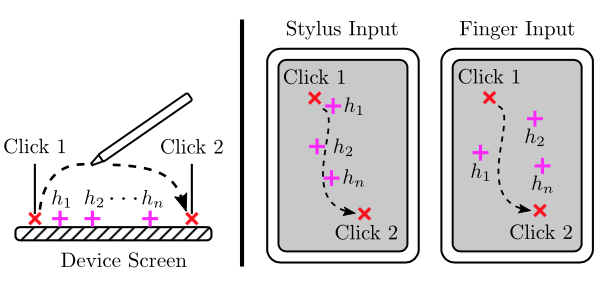
Example of post-click hover events collected by Hoover. In case of stylus input (center), the post-click hover events captured tend to follow quite faithfully the stylus path. In case of a finger, the captured hover events are scattered over a wider area and are rarely directly over the click points.
One of the researchers, Luka Malisa, commented: “Our attack is interesting as it demonstrates how new technologies, that seem benign at first glance, can have unexpected security ramifications. As our attack can be implemented without any special permissions, it also cannot be easily prevented.”
Luka and his colleagues evaluated the attack with 40 users, on two different Android devices and two input methods (stylus and finger). They found that the attack works very accurately in most cases. Full technical details are available in a research paper online: https://arxiv.org/pdf/1611.01477v1.pdf
These research results were covered by a technology news website The Registers: http://www.theregister.co.uk/2016/11/08/androids_hover_/
UPDATE on August 8: See also article from Zurich-based newspaper Tages Anzeiger: http://www.tagesanzeiger.ch/wirtschaft/standardso-konnten-ethforscher-heikle-handydaten-absaugen/story/23341179
