Secure Positioning and Localization
Despite global navigation systems, such as GPS and Galileo, having been widely used for almost two decades, these systems are still vulnerable to signal spoofing attacks. This has become evident in serious incidents, most prominently the hijacking of a US military drone over Iranian territory in 2011. However, location manipulation attacks also pose a risk in existing and future civilian navigation applications, such as autonomous driving.
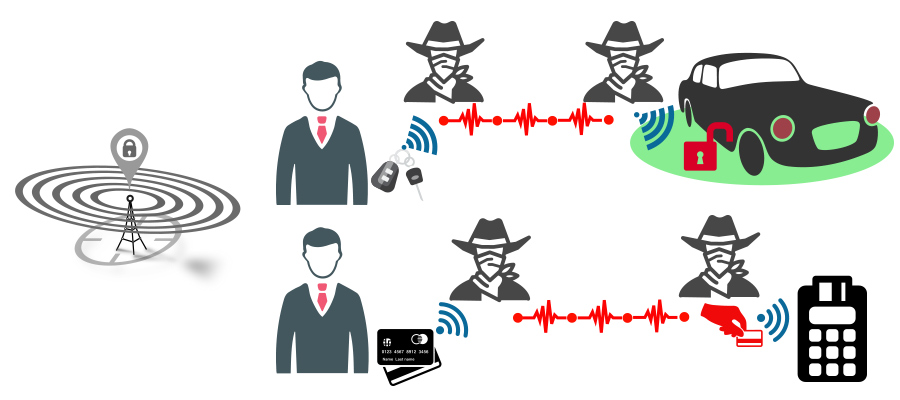
In the context of proximity verification, systems for unlocking cars have been attacked by relaying signals between key and door, in the worst case allowing an attacker to steal a car. Since its first demonstration almost ten years ago, this and similar attacks were in the news multiple times, both as research efforts but also actual thefts. Contributing to the latter trend is the fact that equipment for signal generation is becoming more accessible. Today, it is simpler than ever for an attacker to mount attacks on ranging signals, due to very versatile, programmable signal generation equipment, such as USRPs, becoming cheaper and easier to use. As location information becomes ever more critical in the future due to the increasing prevalence of cyber-physical systems, secure design becomes vital on all protocol layers. This includes how a device measures proximity and location on the physical layer, i.e., on the level of signals.
Our research is concerned with designing localization and proximity-verification systems based on wireless signals that are secure against any known distance-modifying attacker, irrespective of its hardware. We also direct our efforts toward understanding the impact of attacks on existing systems, such as GPS or next-generation air traffic control, and making those systems more robust. Finally, there is an incentive to augment existing systems and protocols with this robust notion of location and proximity, as an added factor for security, such as for authentication in the web.
Below is a list of selected publications related to this field. For the full set of publications, please visit the System Security list of publications.
Selected Publications
Mridula Singh, Patrick Leu, Srdjan Capkun
UWB with Pulse Reordering: Securing Ranging against Relay and Physical-Layer Attacks
in Proceedings of the Network and Distributed System Security Symposium (NDSS), 2019 (to appear)
Hildur Ólafsdóttir, Aanjhan Ranganathan, Srdjan Capkun
On the Security of Carrier Phase-based Ranging
in Proceedings of Cryptographic Hardware and Embedded Systems (CHES), 2017
Aanjhan Ranganathan, Hildur Ólafsdóttir, Srdjan Capkun
SPREE: Spoofing Resistant GPS Receiver
22nd Annual International Conference on Mobile Computing and Networking (MobiCom), 2016
Daniel Moser, Patrick Leu, Vincent Lenders, Aanjhan Ranganathan, Fabio Ricciato, Srdjan Capkun
Investigation of Multi-device Location Spoofing Attacks on Air Traffic Control and Possible Countermeasures
22nd Annual International Conference on Mobile Computing and Networking (MobiCom), 2016
Der-Yeuan Yu, Aanjhan Ranganathan, Ramya Jayaram Masti, Claudio Soriente, Srdjan Capkun
SALVE: Server Authentication with Location VErification
22nd Annual International Conference on Mobile Computing and Networking (MobiCom), 2016
Aanjhan Ranganathan, Boris Danev, Srdjan Capkun
Proximity Verification for Contactless Access Control and Authentication Systems
28th Annual Computer Security Applications Conference (ACSAC), 2015
Nils Ole Tippenhauer, Heinrich Luecken, Marc Kuhn and Srdjan Capkun
UWB Rapid-Bit-Exchange System for Distance Bounding
ACM Conference on Security and Privacy in Wireless and Mobile Networks (WiSec), 2015
Aanjhan Ranganathan, Nils Ole Tippenhauer, Boris Skoric, Dave Singelée, Srdjan Capkun.
Design and Implementation of a Terrorist Fraud Resilient Distance Bounding System
17th European Conference on Research in Computer Security (ESORICS), 2012
Cas Cremers, Kasper Bonne Rasmussen, Benedikt Schmidt, Srdjan Capkun
Distance Hijacking Attacks on Distance Bounding Protocols
IEEE Symposium on Security and Privacy (S&P), 2012
Aanjhan Ranganathan, Boris Danev, Aurélien Francillon, Srdjan Capkun
Physical-layer attacks on chirp-based ranging systems
ACM Conference on Security and Privacy in Wireless and Mobile Networks (WiSec), 2012
Nils Ole Tippenhauer, Christina Pöpper, Kasper Bonne Rasmussen, Srdjan Capkun
On the Requirements for Successful GPS Spoofing Attacks
ACM Conference on Computer and Communications Security (CCS), 2011
Kasper Bonne Rasmussen, Srdjan Capkun
Realization of RF Distance Bounding
USENIX Security Symposium, 2010
Srdjan Capkun, Mario Cagalj, Ghassan Karame, Nils Ole Tippenhauer
Integrity Regions: Authentication Through Presence in Wireless Networks
IEEE Transactions on Mobile Computing (TMC), 2010
Kasper Bonne Rasmussen, Claude Castelluccia, Thomas S. Heydt-Benjamin, Srdjan Capkun
Proximity-based Access Control for Implantable Medical Devices
ACM Conference on Computer and Communications Security (CCS), 2009
Nils Ole Tippenhauer, Kasper Bonne Rasmussen, Christina Pöpper, Srdjan Capkun
Attacks on Public WLAN-based Positioning Systems
ACM/Usenix International Conference on Mobile Systems, Applications and Services (MobiSys), 2009
