Access control
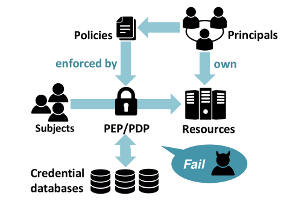
Access control has wide range of applications, including physical access control (e.g., to buildings), access control in single applications, and enterprise-wide access control solutions for an entire company’s data management. Our work encompasses four areas: 1. access control for physical systems, 2. languages for efficiently analyzable yet expressive access control policies, 3. techniques for ensuring that no security-critical access control queries are omited, and 4. mining access control policies from logs.
- Modern physical access control systems are abandoning traditional physical keys and moving towards contactless, Internet-based access media solutions. In recent years, access control systems have vastly benefited from formal languages, which divorce a policy specification from an actual PDP implementation. The increased complexity of these systems in combination with the high-security requirements renders the task of designing and building such access control systems challenging. Our work focusses on the formal specification, verification, and synthesis of access control systems for physical spaces.
-
Different RBAC (Role-based access control) extensions have been proposed over the past few decades. These extensions have brought greater expressiveness in policy specification. However, their added expressiveness has also inadvertently brought greater difficulties in policy analysis. We have developed FORBAC, an extension of RBAC that strikes a balance between expressiveness in policy specification and efficiency in policy analysis.
-
The implementation of business applications is often outsourced to external software development companies who cannot be trusted to implement access control procedures properly. This is one of the reasons why enforcing access control is one of the main issues in OWASP 2015. We are developing methods for checking that before every security relevant section in the code, an authorization request is correctly sent to the PDP. By using static program analysis we will identify missing authorization requests as well as requests submitting altered context information.
-
When organizations become very large, access control lists become impractical for specifying access control policies. At this point, organizations should migrate from access control matrices to ABAC (Attribute-based access control) policies that assign permissions to users according to the users’ and the permissions’ attributes. This migration process requires intensive inspections of the users, the permissions, and the access control matrices and is mainly done manually, which makes it error prone. We are developing procedures for automatically mining attribute-based policies from access control matrices.
Publications
Carlos Cotrini, Thilo Weghorn, David Basin, and Manuel Clavel
Analyzing First-order Role Based Access Control
IEEE Computer Security Foundations Symposium (CSF), 2015
Petar Tsankov, Srdjan Marinovic, Mohammad Torabi Dashti, David Basin
Fail-Secure Access Control
ACM Conference on Computer and Communication Security (CCS), 2014
Petar Tsankov, Srdjan Marinovic, Mohammad Torabi Dashti, David Basin
Decentralized Composite Access Control
ETAPS POST, 2014
Mario Frank, Morteza Haghir Chehreghani and Joachim M. Buhmann
The Minimum Transfer Cost Principle for Model-Order Selection
European Conference on Machine Learning and Principles and Practice of Knowledge Discovery in Databases (ECML PKDD 2011), September 2011.
Mario Frank and Joachim M. Buhmann
Selecting the rank of truncated SVD by Maximum Approximation Capacity
IEEE International Symposium on Information Theory (ISIT 2011), August 2011.
Joachim M. Buhmann, Morteza Haghir Chehreghani, Mario Frank and Andreas P. Streich
Information Theoretic Model Selection for Pattern Analysis
ICML 2011 Workshop on Unsupervised and Transfer Learning, June 2011.
Mario Frank and Ian Molloy
Tutorial on Role Mining
17th ACM Conference on Computer and Communications Security (CCS 2010), October 2010.
Mario Frank, Joachim M. Buhmann and David Basin
On the Definition of Role Mining
15th ACM Symposium on Access Control Models and Technologies (SACMAT 2010), June 2010.
Mario Frank, Andreas P. Streich, David Basin and Joachim M. Buhmann
A Probabilistic Approach to Hybrid Role Mining
16th ACM Conference on Computer and Communications Security (CCS 2009), November 2009.
Andreas P. Streich, Mario Frank, David Basin and Joachim M. Buhmann
Multi-Assignment Clustering for Boolean Data
26th International Conference on Machine Learning (ICML 2009), June 2009
Mario Frank, David Basin and Joachim M. Buhmann
A Class of Probabilistic Models for Role Engineering
15th ACM Conference on Computer and Communications Security (CCS 2008), October 2008.
