Improving Network Security Through Programmability
Status
This project started in 2016 and has been successfully completed in 2022.
Researchers
Roland Meier (ETH)
Laurent Vanbever (ETH)
Vincent Lenders (Armasuisse)
Industry partner
armasuisse
Description
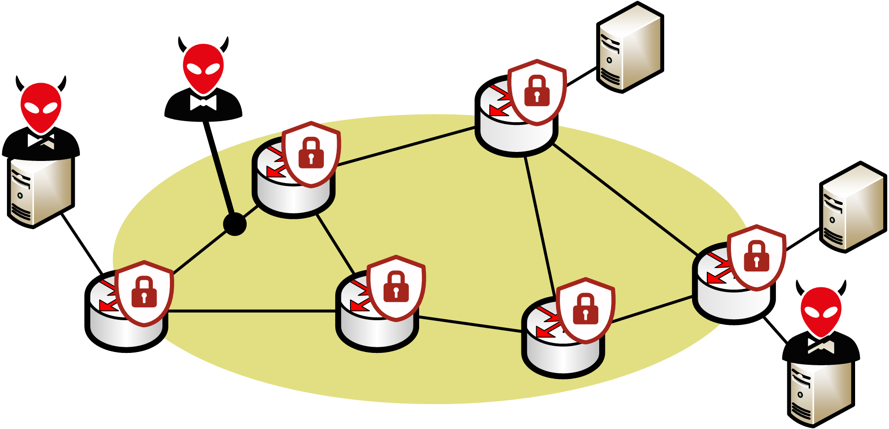
In this project, we argue that the network itself should be able to detect and mitigate attacks instead of relying purely on perimeter-based protection provided by dedicated appliances. To do so, we plan to leverage recent advances in network programmability which enable both the control plane and the data plane to be reprogrammed on-the-fly.
The goal of this project is to leverage recent advances in network programmability to make the network able to defend itself against: (i) anonymity and privacy attacks, performed by attackers which can eavesdrop on and modify traffic; and (ii) more general attacks (e.g., denial-of-service, data exfiltration), performed by attackers sitting at the edge of the network, on compromised hosts.
Protecting networks from in-network attackers: This part of the project aims at designing and developing a network-based anonymity and privacy framework targeted specifically at enterprise networks. Being network-based, the framework will enable to secure any connected devices (even unforeseen ones) and internal communications, without complex setup. To develop this “securing” network, we will actively leverage the new programmability primitives offered by Software-Defined Networks (SDN) in both the control plane (OpenFlow) and the data plane (P4).
Protecting networks from edge attackers: In this part of the project, we focus on attackers that get access to the network via one or more infected hosts. After infecting at least one host, such attackers usually initiate a “reconnaissance” phase in which they scan the network in search of high value targets. Network programmability enables to efficiently distribute the task of scan detection on the network devices and provides the ability to source traffic on the network device in order to implement advanced deception techniques in which the attacker is presented with fake information (e.g., fake IP addresses).
Publications
Roland Meier, Vincent Lenders, Laurent Vanbever
ditto: WAN Traffic Obfuscation at Line Rate
NDSS Symposium 2022. San Diego, CA, USA (April 2022).
Ege Cem Kirci, Maria Apostolaki, Roland Meier, Ankit Singla, Laurent Vanbever
Mass Surveillance of VoIP Calls in the Data Plane
ACM SOSR 2022. Online (October 2022).
Roland Meier, Thomas Holterbach, Stephan Keck, Matthias Stähli, Vincent Lenders, Ankit Singla, Laurent Vanbever
(Self) Driving Under the Influence: Intoxicating Adversarial Network Inputs
ACM HotNets 2019. Princeton, NJ, USA (November 2019).
Roland Meier, Petar Tsankov, Vincent Lenders, Laurent Vanbever, Martin Vechev
NetHide: Secure and Practical Network Topology Obfuscation
USENIX Security 2018. Baltimore, MD, USA (August 2018).
For more details, see: https://nethide.ethz.ch
Roland Meier, David Gugelmann, Laurent Vanbever
iTAP: In-network Traffic Analysis Prevention using Software-Defined Networks
ACM SOSR 2017. Santa Clara, CA, USA (April 2017).
For more details, see: https://itap.ethz.ch
