Skip to content
Critical Infrastructure Security
Status
This project started in Spring 2017 and has been successfully completed.
Researchers
Piet De Vaere (ETH)
Prof. Adrian Perrig (ETH)
Seyedali Tabaeiaghdaei (ETH)
Takayuki Sasaki (NEC)
Toshiki Kobayashi (NEC)
Astha Jada (NEC)
Description
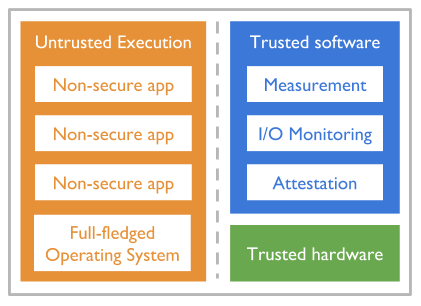
The Internet of things (IoT) describes a plethora of embedded devices which are being built with increasing intelligence (programmability and computational power), and with network connectivity. These devices range from smart light bulbs and door locks in homes to automation and sensing in industrial, healthcare, and military settings. In all these scenarios, the promise of IoT is to enable a large number of new applications, a design space that is being aggressively explored by many platform manufacturers and software development companies. However, IoT also represents a security hazard, due to a lack of proper security engineering in the race to claim fractions of the IoT market segments, and due to inherent challenges such as the dishomogeneity of platforms and operating systems, and the difficulty of keeping deployed devices up to date. One way of improving the security of these IoT devices is through relatively simple yet powerful security primitives embedded in standardized hardware components. These components, together with minimal verified software, can be used as a foundation on which trust in the entire device can be established. An example of this are the Security Extensions of Arm’s embedded architectures, which provide a hardware-isolated environment in which trusted software (e.g., a verified micro-kernel) can be run to secure core functionalities such as security updates, sensitive cryptographic operations, and software measurement primitives which can be used to verify the rest of the software running on the device. More recently, Arm has launched its Platform Security Architecture (PSA) framework, which aims to extend the security functionalities provided by the trusted environments. In this project we plan to investigate how these hardware components and architectures may be used to build powerful software tools for monitoring, enforcement, and recovery on IoT devices, focusing in particular on the most critical IoT use cases in the domains of industry, healthcare and military. Furthermore, through this work we aim to gain a better understanding in more theoretical terms of what types of high-level security primitives can be constructed from a minimal set of hardware-provided functionalities.
Publications
Toshiki Kobayashi, Takayuki Sasaki, Astha Jada, Daniele E. Asoni, and Adrian Perrig. 2018. SAFES: Sand-boxed Architecture for Frequent Environment Self-measurement. In 3rd Workshop on System Software for Trusted Execution (SysTEX ’18), October 15, 2018, Toronto, ON, Canada. ACM, New York, NY, USA, 5 pages. https://doi.org/10.1145/3268935.3268939