Fine-grained Internet Path Control and DDoS Defense
Status:
This project started in March 2023 and is ongoing.
Researchers:
Marc Wyss
Jelte van Bommel
Juan A. García-Pardo
Prof. Dr. Adrian Perrig
Industry Partner:
armasuisse
Description:
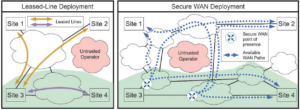
The Network Security group collaborates with armasuisse to build a highly secure WAN infrastructure based on the SCION future Internet architecture, particularly focusing on achieving fine-grained path control and increased communication availability.
In a recent collaboration with armasuisse titled “On Building Secure Wide Area Networks over Public Internet Service Providers,” we investigate the challenges associated with constructing a secure WAN over public Internet infrastructure. We found that some of the most difficult challenges include (i) ensuring communication availability between WAN sites, especially during network congestion induced by DDoS attacks, and (ii) achieving fine-grained path transparency and control. We identified several systems that help mitigate such attacks and assessed their technology readiness level (TRL). This year, our focus will be on enhancing the TRL of these systems while also conducting further research to strengthen WAN communication availability.
Fine-Grained Path Control
We aim to extend SCION’s capabilities of path transparency and control to the intra-domain router level. The idea is to enable network operators to communicate information about their internal router topologies in the form of router policies, which are then made accessible to applications along with a set of selectable forwarding paths. This allows each application to choose suitable router policies and encode the chosen policies within its data packets. In our past collaboration with armasuisse, we designed and analyzed such a system (called FABRID), and subsequently worked on a prototype implementation. This year, we will extend its operational maturity to TRL 6 / 7 by rolling out and deploying a prototype on the SCIONLab infrastructure. We will also investigate incentive mechanisms for ISPs, essentially devising business models that would incentivize ISPs to deploy the system in their infrastructure.
DDoS Defense
We are collaborating on a next-generation bandwidth reservation system. The system’s modular and flexible design allows for novel control planes, such as a control plane implementing a marketplace for bandwidth reservations, and introduces features such as the option to request reservations ahead of time. This year, we will extend the operational maturity of this reservation system to TRL 6/7 by rolling out and deploying a prototype on the SCIONLab infrastructure.
Furthermore, we will conduct research to ensure communication reliability for short-lived intermediate-rate traffic, including DNS communication, command and control system traffic, and access to websites. These types of traffic are challenging to protect using bandwidth reservations.
Since our proposed in-network DDoS defense systems have requirements, for example, related to time synchronization and key distribution, we will also design alternative systems to minimize such requirements while still achieving high communication availability.
Other Directions
In the 5G/6G testbed area, we will continue supporting armasuisse in applying SCION for wide-area experiments. Additionally, in DNS vulnerability analysis and defenses, we will maintain our collaboration through joint supervision of thesis projects. The Network Security Group will also continue supporting armasuisse’s security analysis and pentesting efforts. In this task, we will also assist with coordinating with ISPs and vendors, as well as supporting analyses of testbed deployments.
Publications:
Zero-setup Intermediate-rate Communication Guarantees in a Global Internet,
Marc Wyss and Adrian Perrig,
33rd USENIX Security Symposium (USENIX Security 24)
[PDF]
International Conference on Cyber Conflict (NATO CCDCOE CyCon), 2024.
[PDF]
[PDF]